Challenge 5
Fifth challenge of the Flare CTF around the famous dark net marketplace, Silk Road.
Challenge description
- CTF Name : Flare CTF 2025
- Categories : CTI, Web
- Difficulty : Unknown
- Date : December 22-29, 2025
We are given the following challenge:
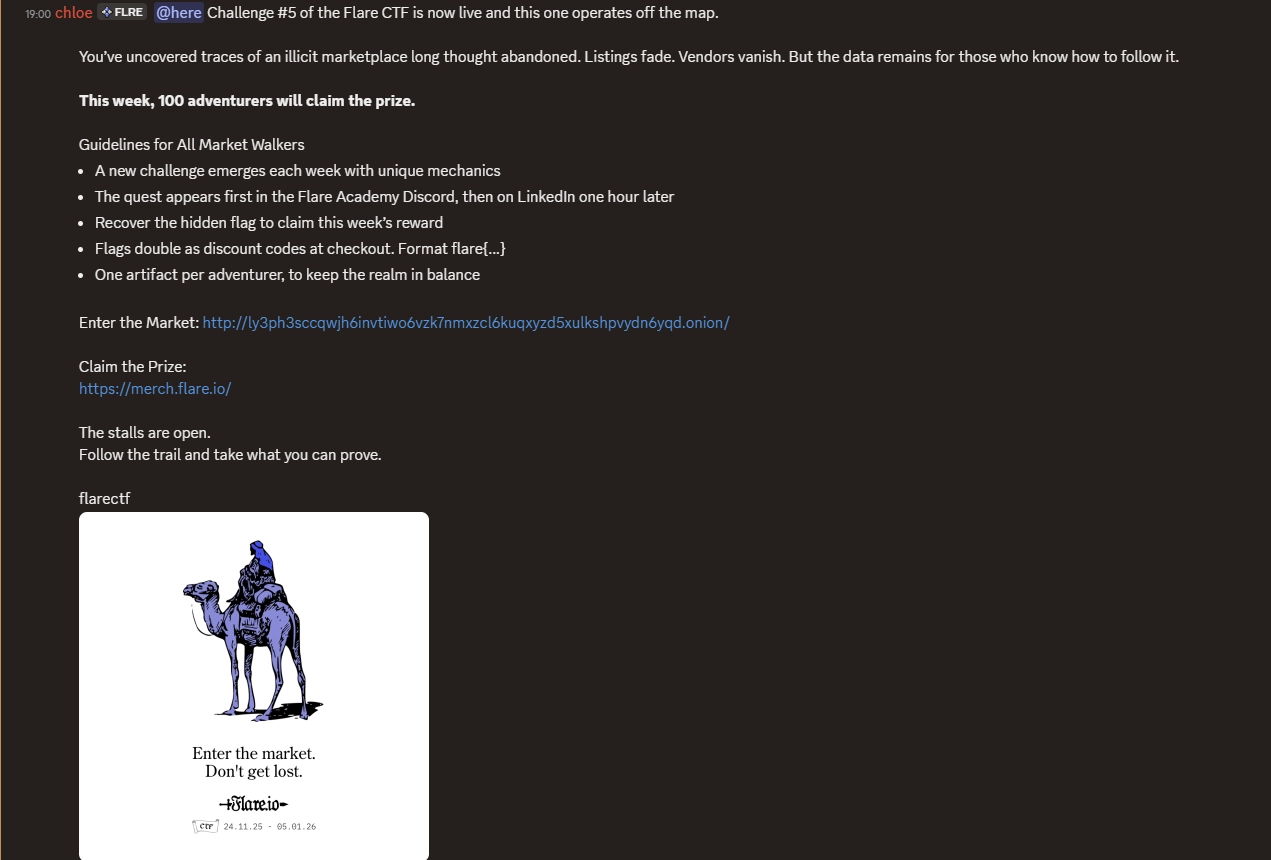
It was time to spin up Tor and see what was behind that onion link.
Digging into the website
The homepage has many products listed. One thing immediately caught my eye was the "FlareCTF Flag LEAKED!" product, sold for 0.15 BTC.
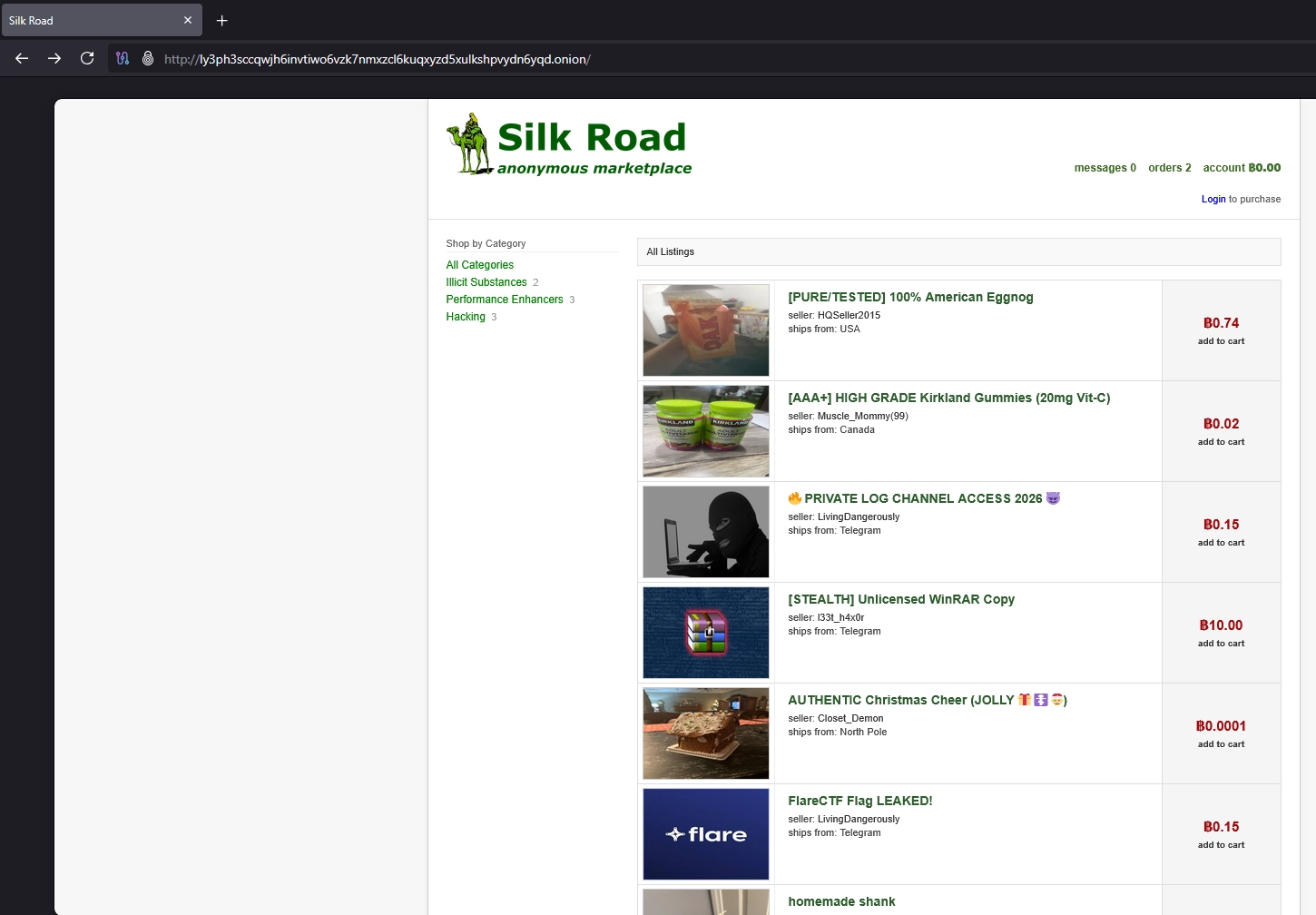
Clicking "add to cart" did nothing. So I guessed I had to be logged in to add products to the cart.
There was no registration page. So I tried to login with the default combo "admin:admin".
That didn't work. But it gave some test credentials : buyer:silkroad
Using them, I was able to log in.
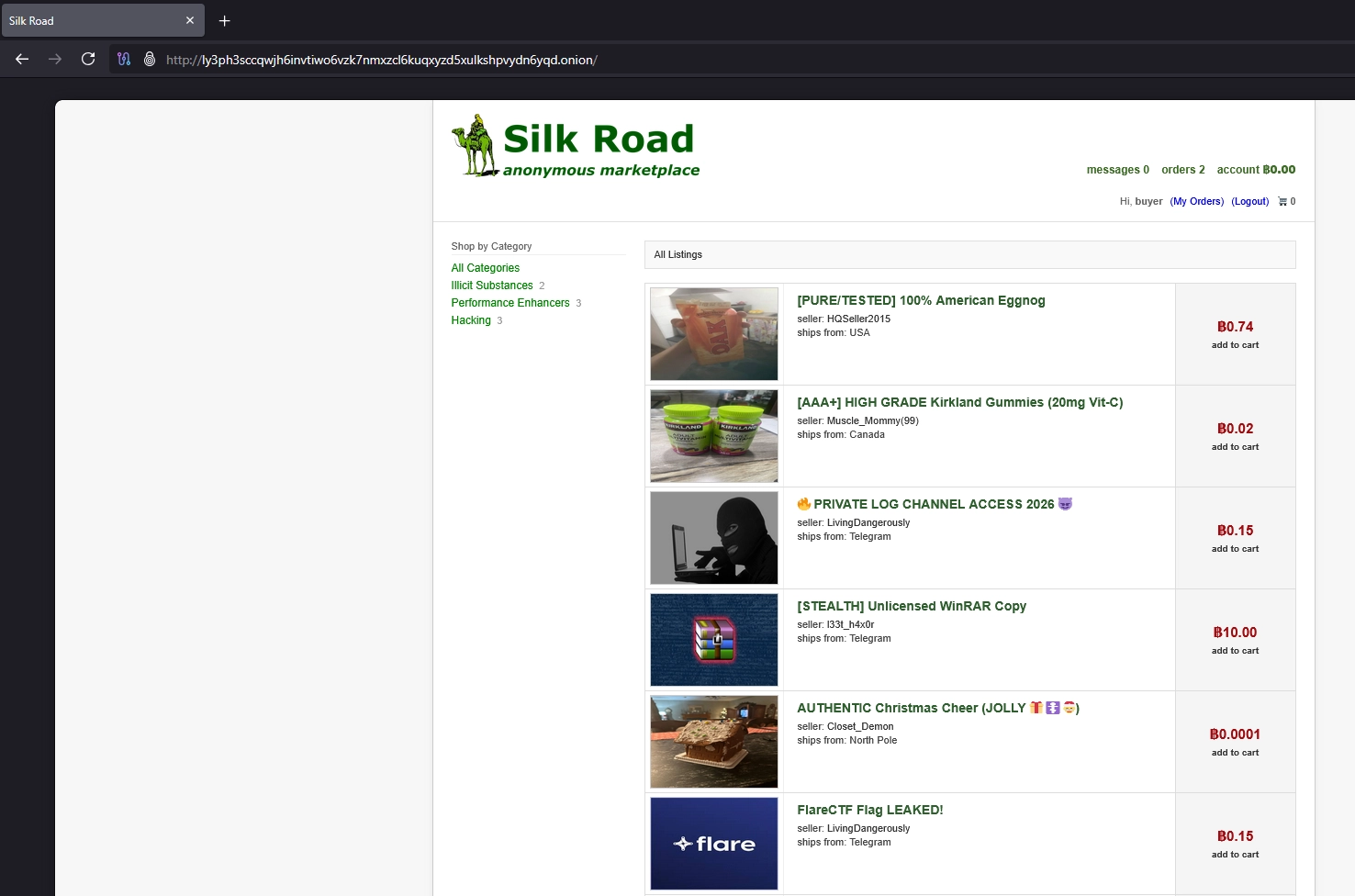
Clicking "add to cart" on the flag product still did nothing. So I decided to check the orders page where two orders were already listed.
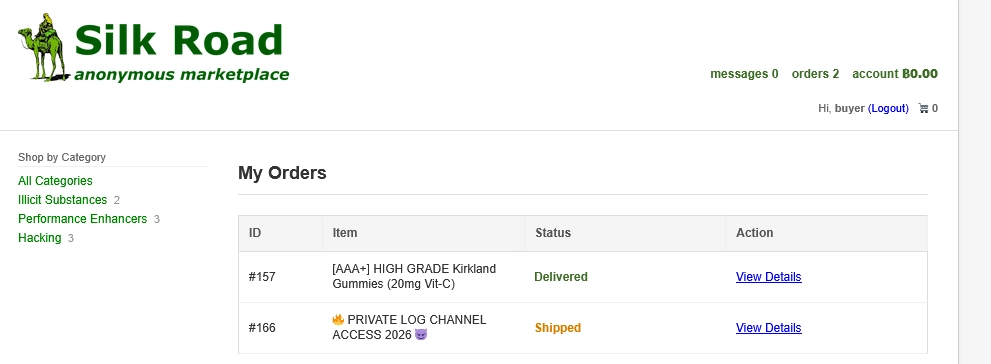
I saw that the order for the item 🔥 PRIVATE LOG CHANNEL ACCESS 2026 😈 was already shipped. The only sellers notes were Check mail., so nothing interesting for now. But I saw another interesting detail : the order page was loaded using the query parameter id. So id=166 for this order. That could be a clear IDOR vulnerability (see OWASP Cheat sheet).
Exploiting the IDOR vulnerability
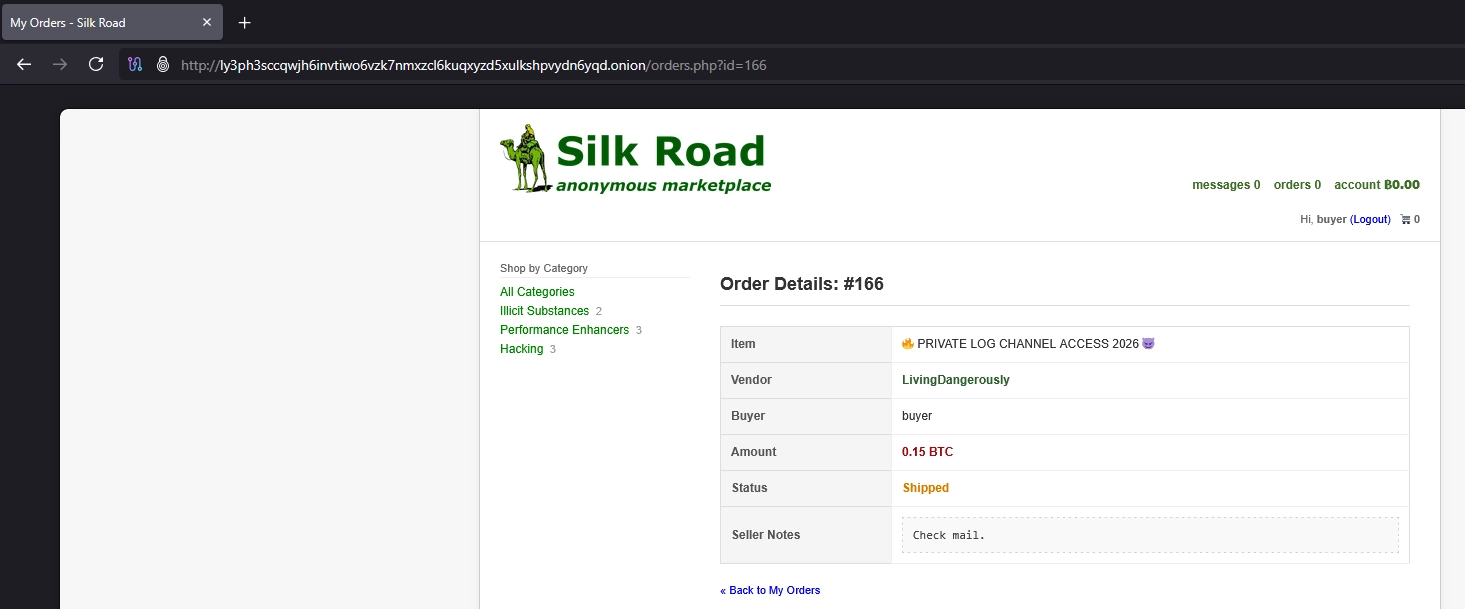 Indeed, by changing the
Indeed, by changing the id parameter incrementally, I was able to access other users' orders. The one to find was id=3.
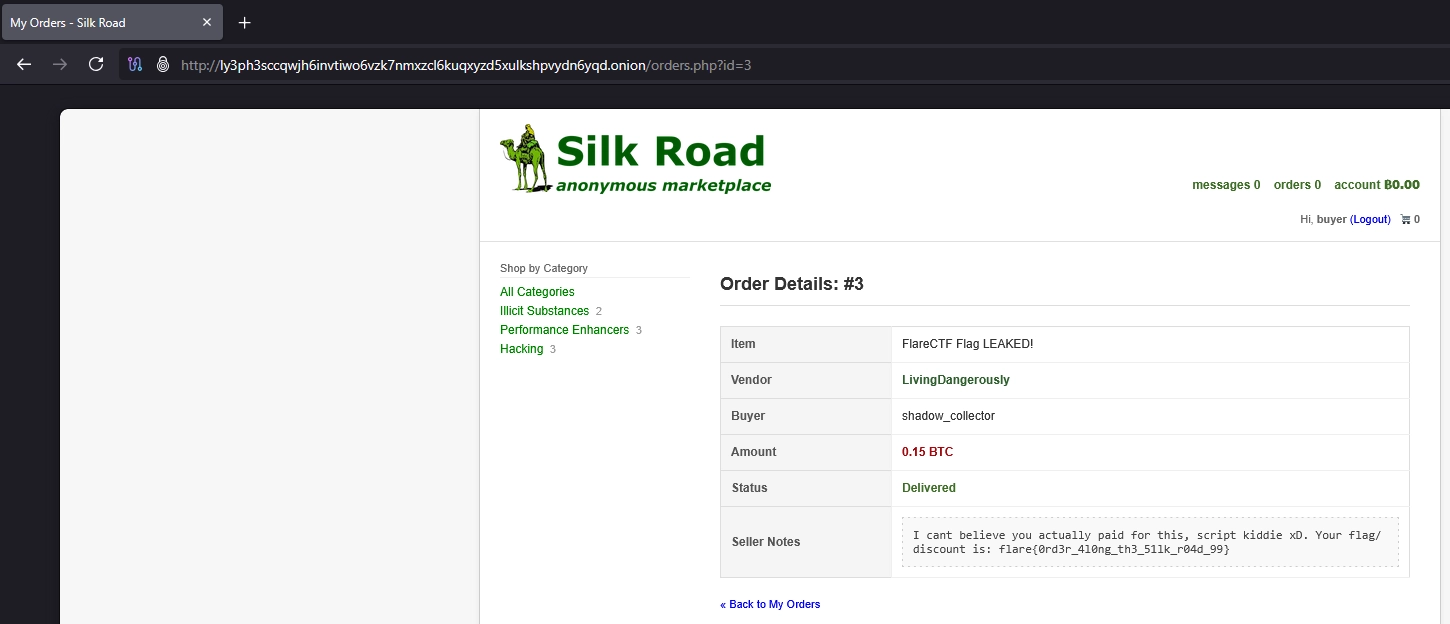
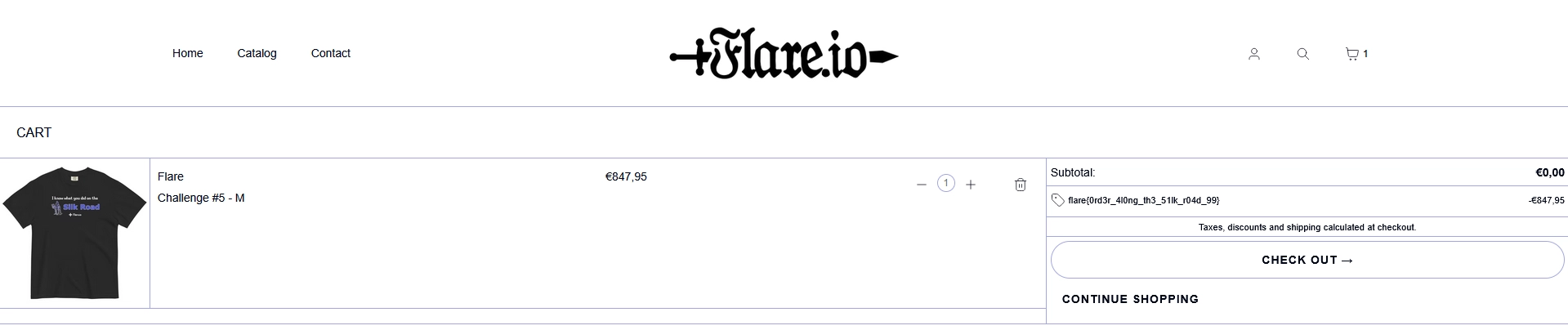
flare{0rd3r_4l0ng_th3_51lk_r04d_99}
Thanks Flare for this nice CTF challenge and t-shirt !