Challenge 6
Sixth challenge of the Flare CTF, let's dig into some forensic analysis !
Challenge description
- CTF Name : Flare CTF 2025
- Categories : CTI, Forensics
- Difficulty : Unknown
- Date : December 29, 2025 - January 5, 2026
We are given the following challenge:
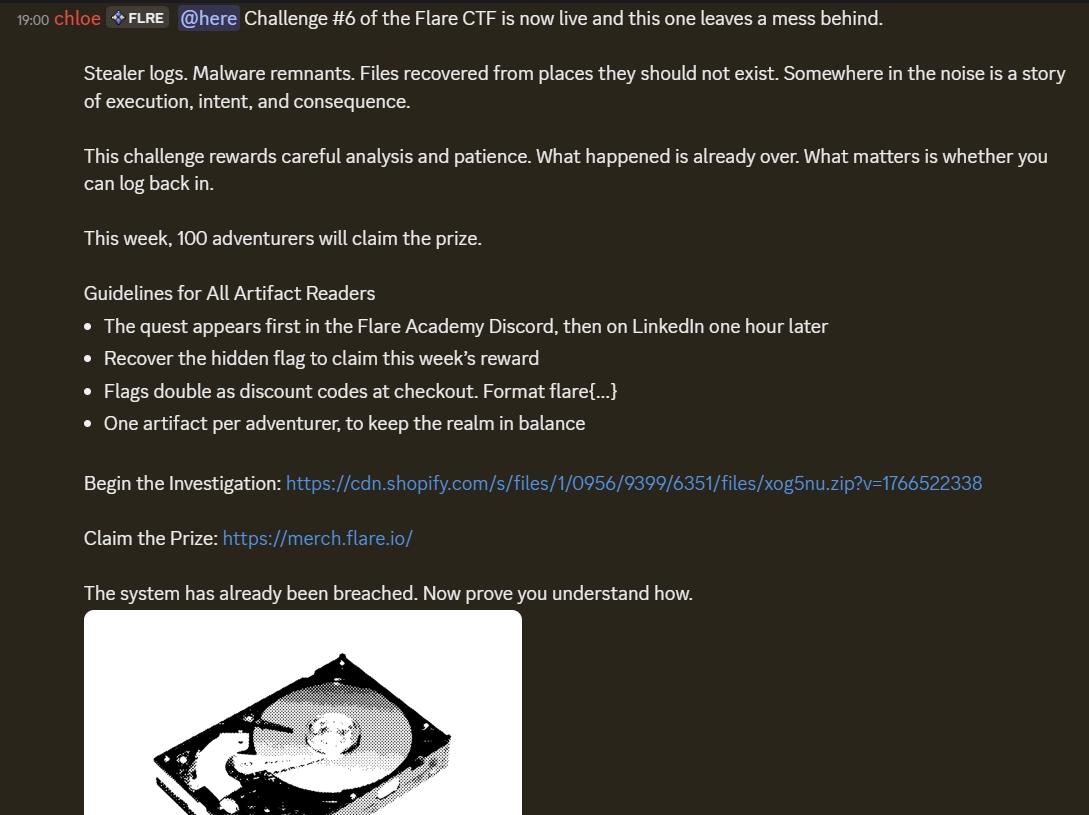
Digging into the forensic challenge
In the archive, we had the following files. One of them was a screenshot:
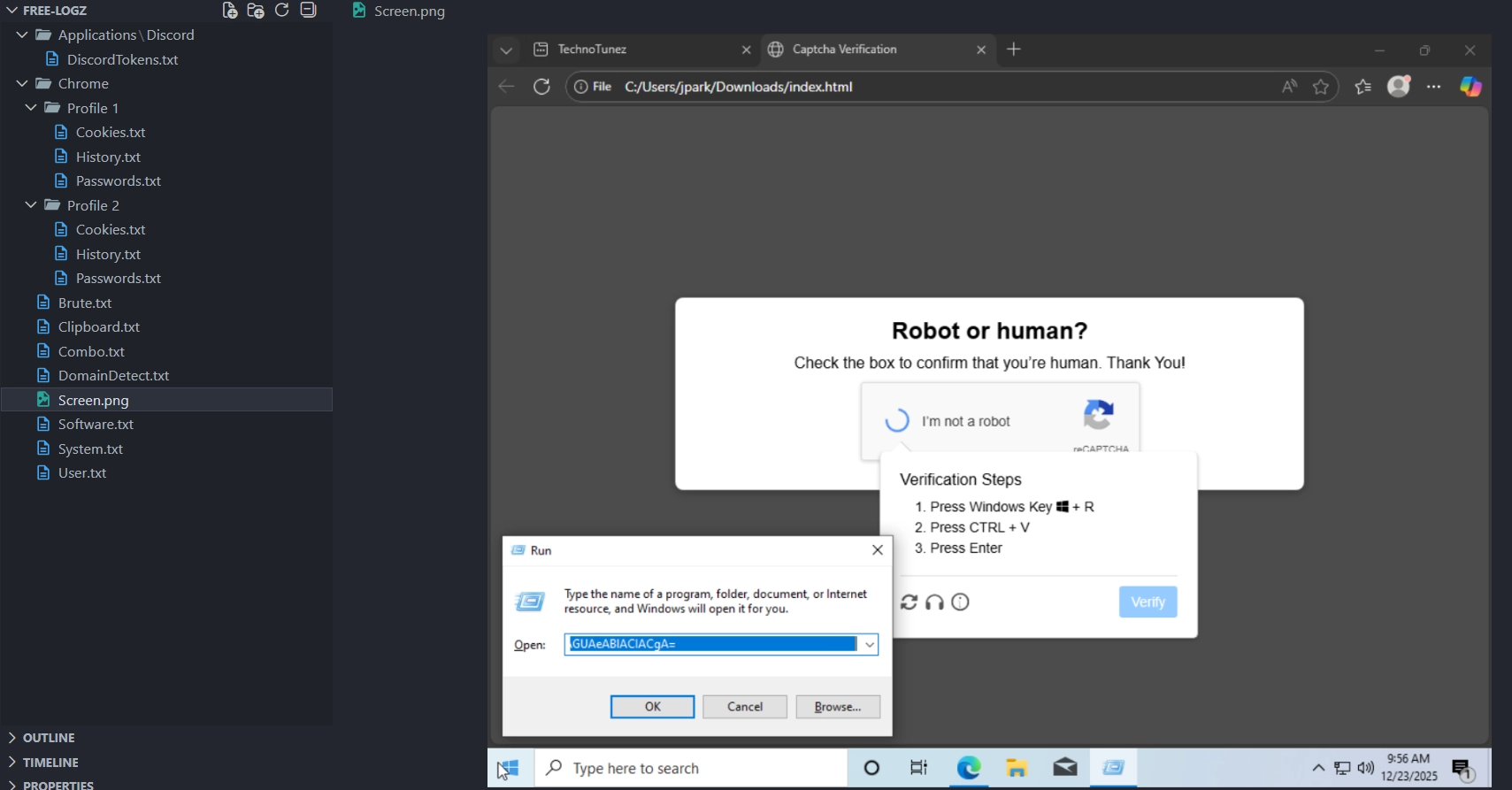
We can see :
- A Run window dialog box with the end of what seems to be a base64 string.
- In the Edge browser, a tab with the name
Technotunez - The current time is
9:56 AMon12/23/2025.
Browsing into the archive, we also have a file named DiscordTokens.txt which contains a Discord token. Thus, I tried to download all the messages using DiscordChatExporter.
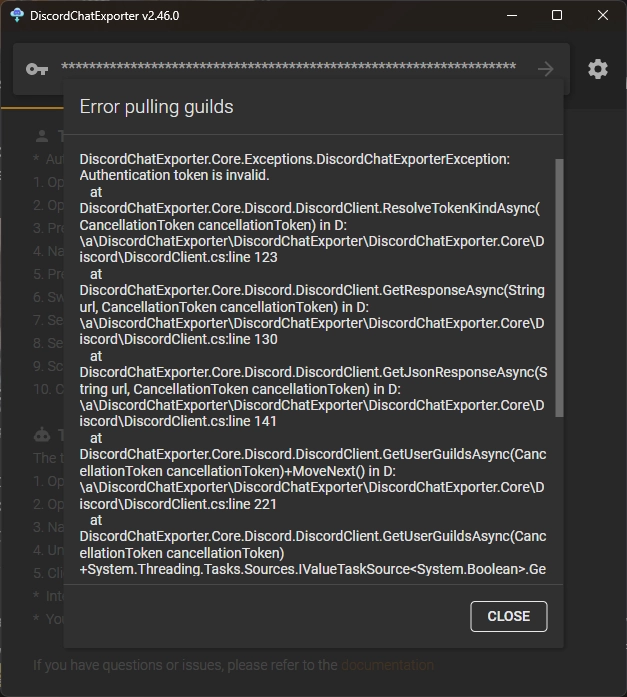
Unfortunately, it didn't work.
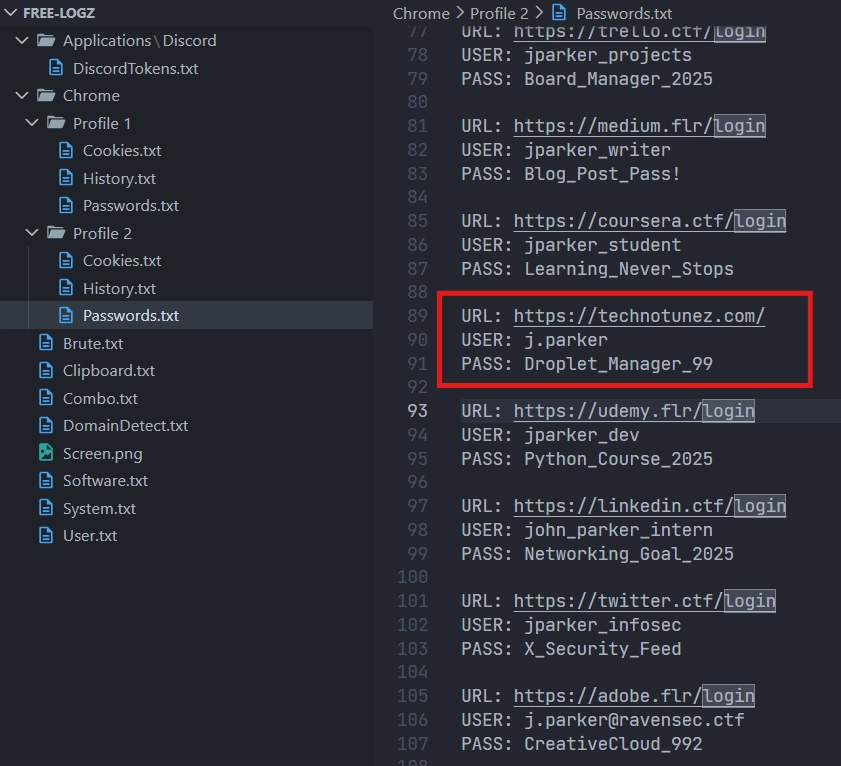
Then, I saw all the different files containing usernames and passwords. One of them was for the previous website Technotunez, thus I decided to try to log in with the combo j.parker:Droplet_Manager_99.
It worked but I needed a 2FA code.
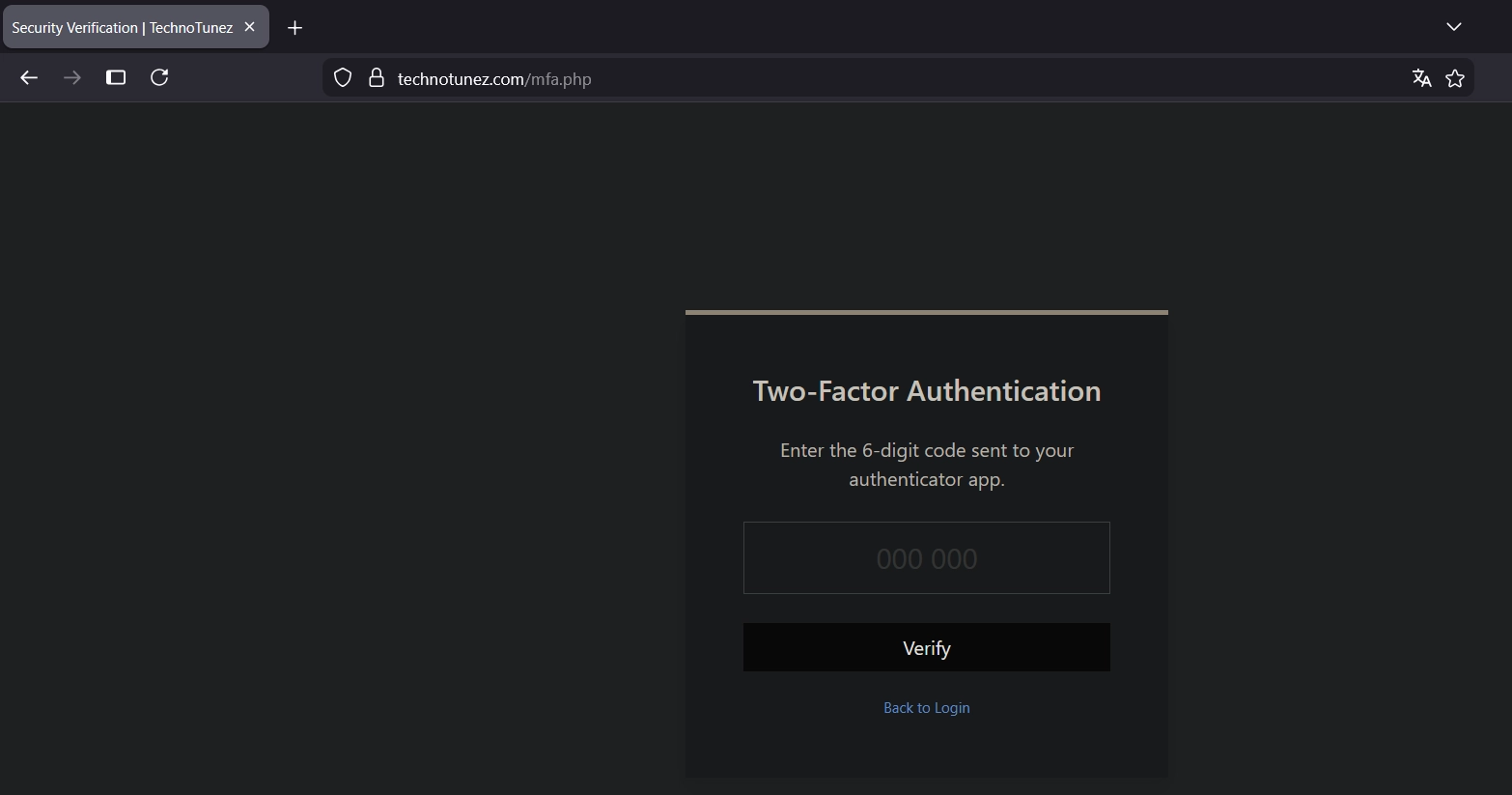
I could try to bruteforce it but we may have a better way.
One of the other files was Cookies.txt in the Chrome/Profile 2 directory. I could see two cookies linked to technotunez.com. The most interesting one is the session cookie.
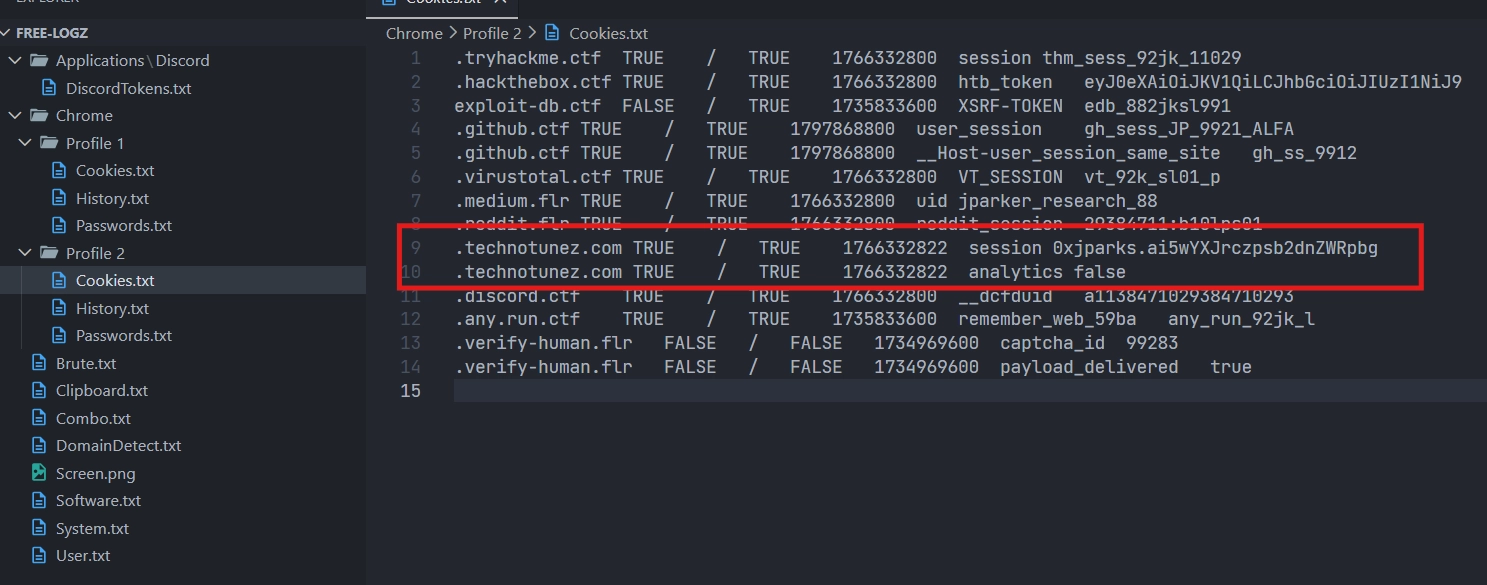
So let's try to insert it into Firefox and log in.
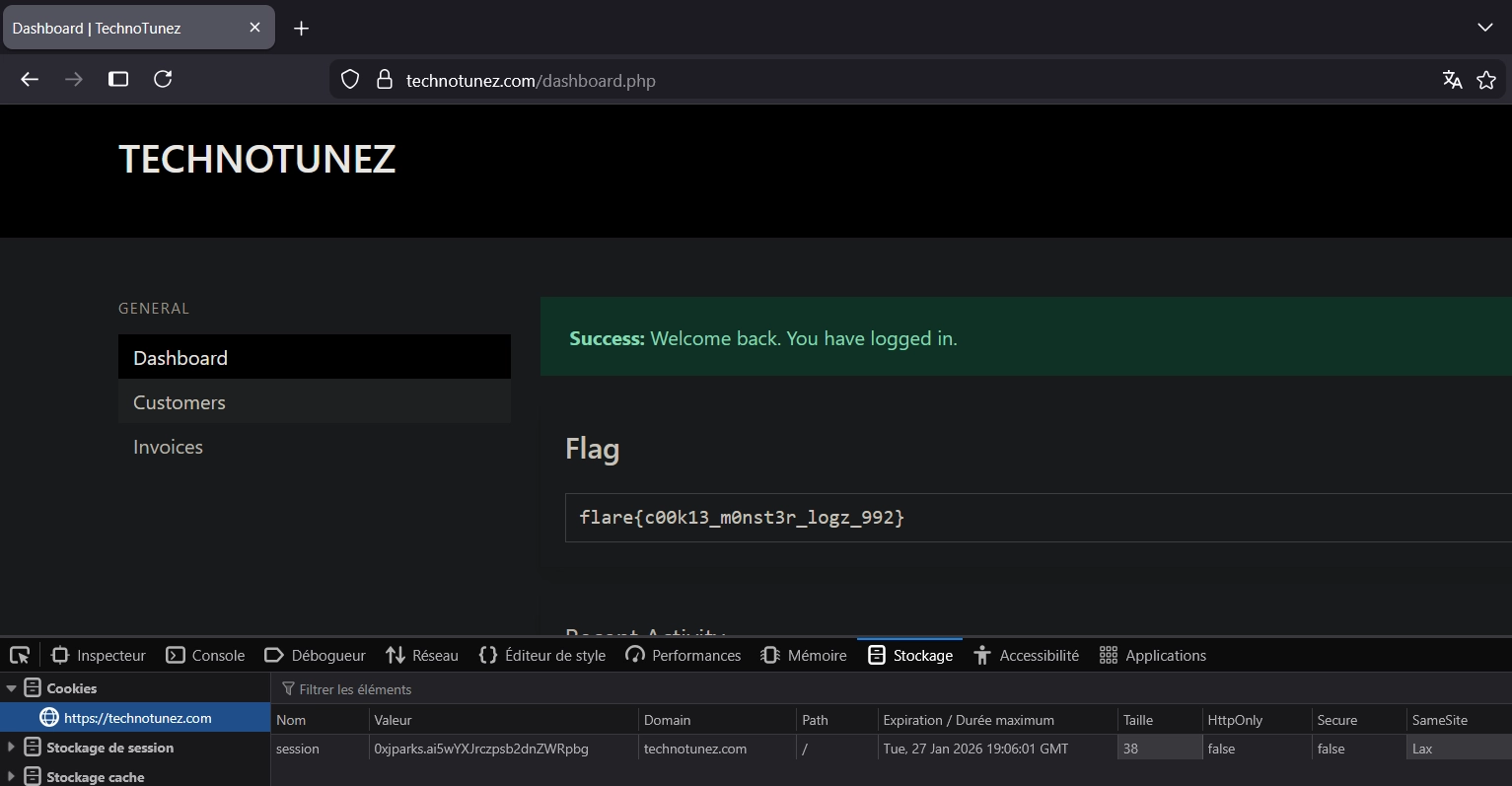
It worked !
flare{c00k13_m0nst3r_logz_992}